What should you about Token Based Authentication?
Hey geeks,
I know you will have already heard the term 'Authentication’. Today, I’m going to deeply explain all the important points about 'Token Based Authentication' which everyone should know before using it while developing the software.
First, we should learn about the difference between the terms - Authentication and Authorization?
Authentication and Authorization are different but related terms. Simply, Authentication is a process of verifying who the person is while Authorization is a process of checking what type of access the person has?
Let’s learn about - Token Based Authentication.
- Token Bases Authentication is a protocol which allows user to verify their identity and in return we will provide then an unique token having limited lifecycle.
- During the valid lifecycle of the token, the user can access the software for which the token is generated without re-enter the credentials (username and password).
- It provides second layer of security to the software. Administrator has whole control over each action and transaction.
Demerits of the traditional way of Authentication?
- The user has to remember all the unique passwords. That’s why the user used to write them and it can become a reason for password-theft.
- People used to repeat the same password for different websites. If the attacker gets one password then it’s over for the user.
- People are tired of entering the credentials again and again. So, Token Based Authentication came as the best alternative for it.
Types of Authentication Tokens?
- Connected Token:
- These tokens need to be physically connected to a device, like a USB token you plug into your computer.
- It’s like using a key to open a door – you need to insert it into the lock to gain access.
- Once connected, the token interacts directly with the device to perform its function, such as authentication or data transfer.
2. Disconnected Token:
- Disconnected tokens, on the other hand, don’t need to be physically connected to a device.
- They work wirelessly, similar to a remote control for your TV.
- These tokens can communicate with devices from a distance, making them convenient for tasks like access control or payment without needing direct physical contact.
3. Contactless Token:
- Contactless tokens are a specific type of disconnected token that operates without physical contact.
- They use technologies like RFID (Radio Frequency Identification) or NFC (Near Field Communication) to transmit information wirelessly.
- Just like tapping your phone on a payment terminal to make a contactless payment, these tokens can communicate with compatible devices without needing to be inserted or swiped.
Lifecycle of Tokens?
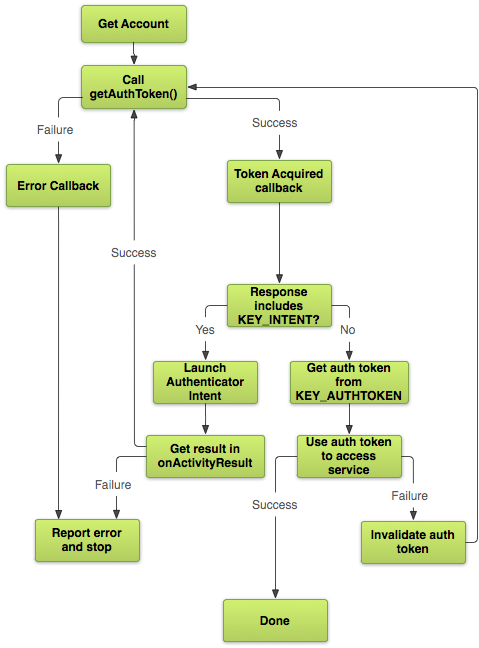
- Request Initiation: The authentication process begins when a client (such as a user’s device or application) sends a request to access a protected resource or service.
- Token Generation: Upon receiving the request, the server generates a unique authentication token. This token serves as proof of the client’s identity and grants access to the requested resource.
- Token Transmission: The server sends the authentication token back to the client as part of the response. This token is typically included in the HTTP headers or as a cookie.
- Token Storage: The client stores the authentication token securely, often in local storage or memory. This allows the client to present the token for future authentication requests without needing to re-enter credentials.
- Token Presentation: When the client makes subsequent requests to access protected resources, it presents the authentication token to the server. This token acts as a digital credential, verifying the client’s identity.
- Token Validation: Upon receiving the authentication token, the server validates its authenticity and integrity. This involves verifying the token’s signature, expiration date, and other relevant information to ensure it hasn’t been tampered with.
- Resource Access: If the authentication token is valid, the server grants access to the requested resource or service. The client can now interact with the resource as authorized.
- Token Refresh: Depending on the token expiration policy, the client may need to refresh the authentication token periodically. This involves requesting a new token from the server using a refresh token or similar mechanism.
- Token Revocation: In some cases, the server may revoke or invalidate an authentication token before its expiration date. This could happen due to security concerns, such as a compromised token or a user logout.
- End of Lifecycle: The lifecycle of the authentication token ends when it expires, is revoked, or when the user logs out. At this point, the client may need to repeat the authentication process to obtain a new token for continued access.
In conclusion, token-based authentication offers a robust and efficient solution for securing web applications and APIs. By following the lifecycle outlined above, developers can implement a reliable authentication mechanism that protects sensitive resources while providing a seamless user experience.
As technology continues to evolve, understanding and leveraging token-based authentication will remain essential in safeguarding digital assets and ensuring trust in the online ecosystem.
